client_credentials and password (Resource Owner Password Credentials).
An OAuth2 credentials configuration file must be stored in the folder configured by the property plantuml.security.credentials.path. The file extension is .credential, the file content is structured in JSON, the charset encoding is UTF-8, the filename must match the UserInfo part of the URL.
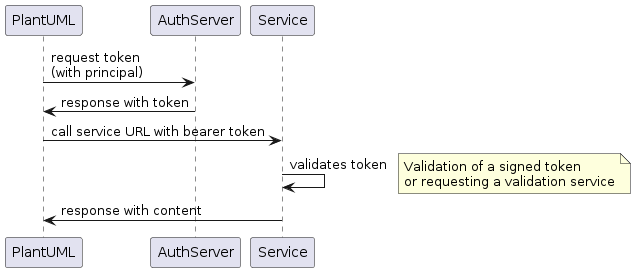
OAuth2 client_credentials JSON structure:
{
"name": "<name of the configuration>",
"type": "oauth",
"identifier": "<principal identifier>",
"secret": "<principal secret>",
"properties": {
"grantType": "client_credentials",
"accessTokenUri": "<URL to token access controler>",
"scope": "<access scopes>"
},
"proxy": {
"type": "<proxy type>",
"address": "<proxy server address>",
"port": "<proxy server port>"
}
}
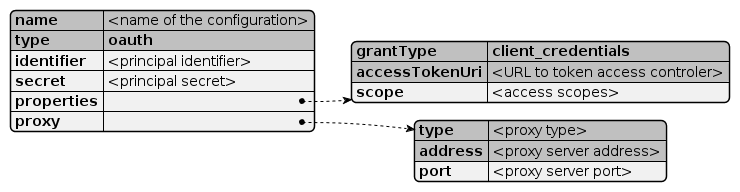
name: required type: oauth requiredidentifier: requiredsecret: properties.grantType: client_credentials requiredproperties.accessTokenUri: requiredproperties.scope: read write)proxy: proxy.type: required (direct, socks, http)proxy.address: requiredproxy.port:
{
"name": "curity-demo",
"type": "oauth",
"identifier": "demo-backend-client",
"secret": "MJlO3binatD9jk1",
"properties": {
"grantType": "client_credentials",
"scope": "read write",
"accessTokenUri": "https://login-demo.curity.io/oauth/v2/oauth-token"
}
}
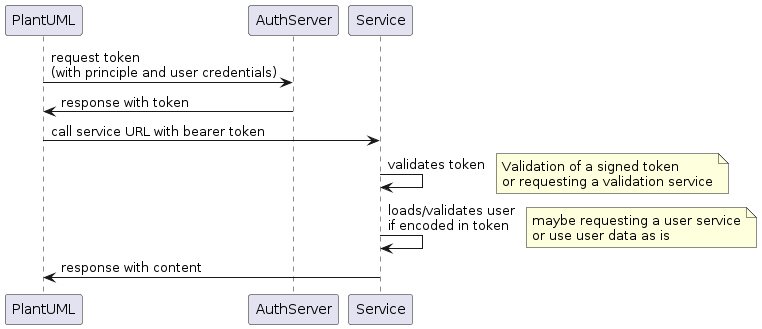
OAuth2 password JSON structure:
{
"name": "<name of the configuration>",
"type": "oauth",
"identifier": "<principal identifier>",
"secret": "<principal secret>",
"properties": {
"grantType": "password",
"accessTokenUri": "<URL to token access controler>",
"scope": "<access scopes>",
"resourceOwner": {
"identifier": "<resource owner name>",
"secret": "<resource owner secret>"
}
},
"proxy": {
"type": "<proxy type>",
"address": "<proxy server address>",
"port": "<proxy server port>"
}
}
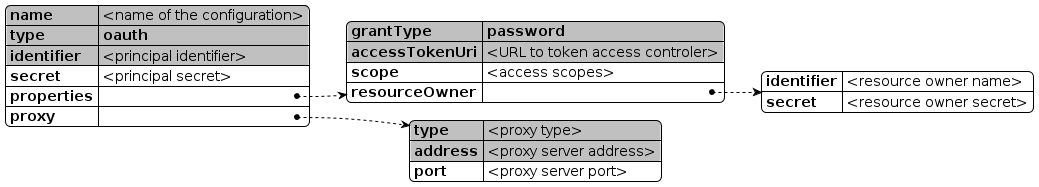
name: required type: oauth requiredidentifier: requiredsecret: properties.grantType: password requiredproperties.accessTokenUri: requiredproperties.scope: read write)properties.resourceOwner.identifier: properties.resourceOwner.secret: proxy: proxy.type: required (direct, socks, http)proxy.address: requiredproxy.port:
{
"name": "oauth-example",
"type": "oauth",
"identifier": "demo-backend-client",
"secret": "MJlO3binatD9jk1",
"properties": {
"grantType": "password",
"scope": "read write",
"accessTokenUri": "https://login-demo.curity.io/oauth/v2/oauth-token",
"resourceOwner": {
"identifier": "alice",
"secret": "secret"
}
}
}
(Please note, login-demo.curity.io actually stopped the support for 'password' grant type)